Google Chrome Enable Key Generation
In-Browser Installation of Client Certificates
Sign in - Google Accounts. Use the chrome.enterprise.platformKeys API to generate hardware-backed keys and to install certificates for these keys. The certificates will be managed by the platform and can be used for TLS authentication, network access or by other extension through chrome.platformKeys. If you have a need for F-keys, don’t fret, you can convert your Chromebook’s shortcut keys into F-keys by following these steps: Click the Settings panel in the bottom right corner of your Chromebook screen. In the resulting Settings menu, choose Settings. This loads your Chromebook settings into a Chrome browser window. Small programs that add new features to your browser and personalize your browsing experience.
GlobalSign offers different certificate delivery methods for PersonalSign products, one of which is installing directly through the browser. Enterprise PKI administrators can set the default delivery option in their ePKI profile.
- Google Cloud Platform.
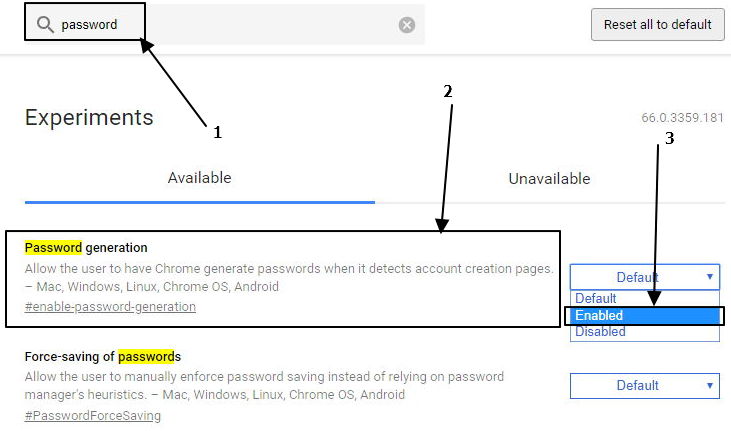
- Jul 08, 2019 Google Chrome offers to save passwords for all your online accounts. It then stores and syncs them to your Google account as part of the Smart Lock feature. Chrome also has a built-in password generator that automatically creates strong passwords at the click of a button.
Shortcut Keys Google Chrome
(A) clicking to accept or agree to the Terms, where this option is made available to you by Google in the user interface for any Service;. teranex 2d processor manual (B) by actually using the Services. In this case, you understand and agree that Google will treat your use of the Services as acceptance of the Terms from that point onwards. /generate-private-key-for-prtg-on-windows-10.html.
Individuals ordering from our retail site can choose this option by clicking Show Advanced Key Generation Options and choosing I will create the public/private keypair and CSR with Firefox or Internet Explorer.
Browser Compatibility
| PKCS #12 (.pfx) Pickup | Browser-Based Installation | PKCS #10 (Provide CSR) |
|---|---|---|
| Google Chrome 1 - 48 | ||
| Google Chrome 49+ | ||
| Microsoft Internet Explorer | ||
| Microsoft Edge | ||
| Mozilla Firefox |
Google Chrome: As of Chrome 49, the <keygen> function has been disabled by default and digital certificate file types are downloaded instead of installed. While the keygen function can manually be enabled, the custom filetype handling is still removed, therefore installation through Google Chrome is not supported.
Microsoft Internet Explorer: IE uses the CertEnroll/XEnroll ActiveX control to generate and install certificates through the browser.
Microsoft Edge: Neither the <keygen> nor the CertEnroll/XEnroll ActiveX controls are present in Microsoft's new Edge browser.
Mozilla Firefox: This browser supports key generation and certificate installation by default through the <keygen> function and special certificate file type handling.
Note:While Firefox supports in-browser certificate installation, it uses its own keystore to store the certificate and is not shared with other applications. Installing through Internet Explorer will install the certificate to the Windows Certificate Store which is used by other applications such as Microsoft Office, Outlook, and Google Chrome. For this reason, Internet Explorer is recommended and is used in the example screenshots.
Instructions
Note: The default Cryptographic Service Provider should be Microsoft Enhanced Cryptographic Provider v1.0. Other providers may appear in the dropdown if you use smartcards in your environment. Selecting your smart card's CSP, such as Microsoft Base Smart Card Crypto Provider will install the certificate onto the smart card.
- When a PersonalSign certificate is ready for pickup, an e-mail will be sent out. Open the link from the pickup e-mail in Internet Explorer or Firefox to start the certificate pickup process.
- Enter the pickup password created during the ordering process:
- When prompted, click Yes to allow your browser to handle a digital certificate operation.
- Unless disabled at the profile level by your admin, check the box to mark your key as exportable. This will allow you to make backups of your certificate or move it to other computers and devices as needed.
- Agree to the subscriber agreement and press Next to continue.
- A Wait for a while. message will display while the certificate is being generated.
- Once the certificate is generated, click Install Certificate
- You will get another prompt to allow your browser to handle a digital certificate operation. Click Yes.
- An Install Success window will appear when the operation completes successfully.
The certificate is now installed and ready for use.
 New Users: Before you can start using the Google Maps Platform APIs and SDKs, you must sign up and create a billing account.To learn more, see Get Started with Google Maps Platform.
New Users: Before you can start using the Google Maps Platform APIs and SDKs, you must sign up and create a billing account.To learn more, see Get Started with Google Maps Platform.To use the Maps Embed API you must have an API key. The API key is a unique identifier that isused to authenticate requests associated with your project for usage and billing purposes.
Get the API key
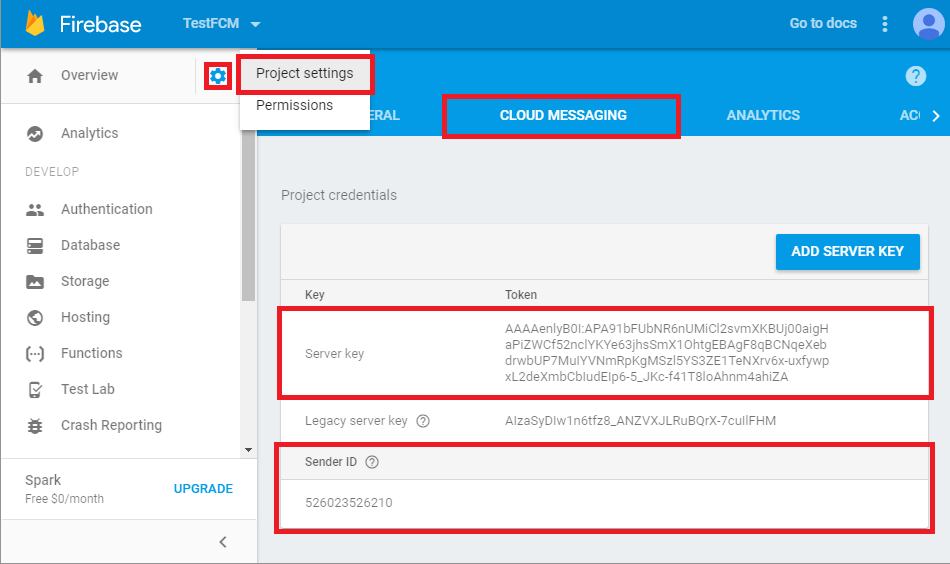
You must have at least one API key associated with your project.
To get an API key:
- Visit the Google Cloud Platform Console.
- Click the project drop-down and select or create the project for which you want to add an API key.
- Click the menu button and select APIs & Services > Credentials.
- On the Credentials page, click Create credentials > API key.
The API key created dialog displays your newly created API key. - Click Close.
The new API key is listed on the Credentials page under API keys.
(Remember to restrict the API key before using it in production.)
Media Keys Google Chrome
Add the API key to your request
You must include an API key with every Maps Embed API request.In the following example, replace YOUR_API_KEY withyour API key.
For more information about MODE and parameters options in the code above, see Forming the URL for the Maps Embed API.
Restrict the API key
We strongly recommend that you restrict your API key. Restrictions provide added security and helpensure only authorized requests are made with your API key. There are two restrictions. You shouldset both:
Google Chrome Enable Key Generation Computer
- Application restriction: Limits usage of the API key to either websites (HTTP referrers), web servers (IP addresses), or mobile apps (Android apps or iOS apps). You can select only one restriction from this category, based on the platform of the API or SDK (see GMP APIs by Platform).
Note: If you need to call web, web service, and/or mobile APIs from the same (client-side) app, create and restrict multiple keys.
- API restriction: Limits usage of the API key to one or more APIs or SDKs. Requests to an API or SDK associated with the API key will be processed. Requests to an API or SDK not associated with the API key will fail. (The API or SDK must be enabled and must support the application restriction.)
Google Chrome Enable Key Generation 7
To restrict an API key:
Chrome Enable Key Generation
- Go to the Google Cloud Platform Console.
- Click the project drop-down select the project that contains the API key you want to secure.
- Click the menu button and select APIs & Services > Credentials.
- On the Credentials page, click the name of the API key that you want to secure.
- On the Restrict and rename API key page, set the restrictions:
- Application restrictions
- Select HTTP referrers (web sites).
- Add the referrers.
- API restrictions
- Select Restrict key.
- Click Select APIs and select Maps Embed API.
(If the Maps Embed API is not listed, you need to enable it.) - Click SAVE.