Command To Generate Hash Key
Oct 04, 2013 I need to generate a md5 hash for given string. It will be used by shell script to generate keys for remote web service or cryptographic application. How do I generate a md5 hash based on any input string under Linux or Unix like operating systems? You can use md5sum command to compute and check MD5 message digest. This is a default tool on. Get File hashes using Windows PowerShell If you need to generate the hash of a file quickly on a Windows machine, then you may also use PowerShell for that. It may not be as comfortable as some of the hashing programs out there, but it is a native implementation that does not require third-party software to work. Nov 14, 2019 There’s loads of other ways that you can create a random password from the command line in Linux—for instance, the mkpasswd command, which can actually assign the password to a.
-->Syntax
Description
The Get-FileHash cmdlet computes the hash value for a file by using a specified hash algorithm.A hash value is a unique value that corresponds to the content of the file. Rather than identifyingthe contents of a file by its file name, extension, or other designation, a hash assigns a uniquevalue to the contents of a file. File names and extensions can be changed without altering thecontent of the file, and without changing the hash value. Similarly, the file's content can bechanged without changing the name or extension. However, changing even a single character in thecontents of a file changes the hash value of the file.
The purpose of hash values is to provide a cryptographically-secure way to verify that the contentsof a file have not been changed. While some hash algorithms, including MD5 and SHA1, are no longerconsidered secure against attack, the goal of a secure hash algorithm is to render it impossible tochange the contents of a file -- either by accident, or by malicious or unauthorized attempt -- andmaintain the same hash value. You can also use hash values to determine if two different files haveexactly the same content. If the hash values of two files are identical, the contents of the filesare also identical.
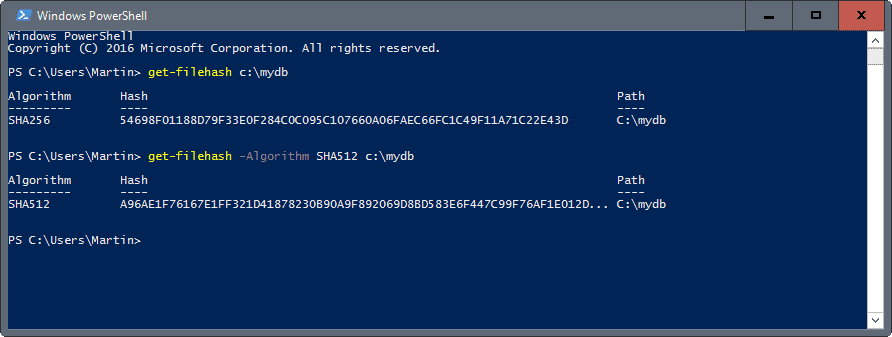
By default, the Get-FileHash cmdlet uses the SHA256 algorithm, although any hash algorithm thatis supported by the target operating system can be used.
Examples
Example 1: Compute the hash value for a file
This example uses the Get-FileHash cmdlet to compute the hash value for the/etc/apt/sources.list file. The hash algorithm used is the default, SHA256. The output ispiped to the Format-List cmdlet to format the output as a list.
Stellar phoenix outlook pst repair key generator. Example 2: Compute the hash value for an ISO file
This example uses the Get-FileHash cmdlet and the SHA384 algorithm to compute the hash valuefor an ISO file that an administrator has downloaded from the internet. The output is piped to theFormat-List cmdlet to format the output as a list.
Example 3: Compute the hash value of a stream
For this example, we get are using System.Net.WebClient to download a package from thePowershell release page. The releasepage also documents the SHA256 hash of each package file. We can compare the published hash valuewith the one we calculate with Get-FileHash.
Example 4: Compute the hash of a string
PowerShell does not provide a cmdlet to compute the hash of a string. However, you can write astring to a stream and use the InputStream parameter of Get-FileHash to get the hash value.
Parameters

Specifies the cryptographic hash function to use for computing the hash value of the contents of thespecified file or stream. A cryptographic hash function has the property that it is infeasible tofind two different files with the same hash value. Hash functions are commonly used with digitalsignatures and for data integrity. The acceptable values for this parameter are:
- SHA1
- SHA256
- SHA384
- SHA512
- MD5
If no value is specified, or if the parameter is omitted, the default value is SHA256.
For security reasons, MD5 and SHA1, which are no longer considered secure, should only be used forsimple change validation, and should not be used to generate hash values for files that requireprotection from attack or tampering. serial key for auslogics bootspeed 8
| Type: | String |
| Accepted values: | SHA1, SHA256, SHA384, SHA512, MD5 |
| Position: | 1 |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the input stream.
| Type: | Stream |
| Position: | 0 |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the path to a file. Unlike the Path parameter, the value of the LiteralPathparameter is used exactly as it is typed. No characters are interpreted as wildcard characters. Ifthe path includes escape characters, enclose the path in single quotation marks. Single quotationmarks instruct PowerShell not to interpret characters as escape sequences.
| Type: | String[] |
| Aliases: | PSPath, LP |
| Position: | 0 |
| Default value: | None |
| Accept pipeline input: | True (ByPropertyName) |
| Accept wildcard characters: | False |
Specifies the path to one or more files as an array. Wildcard characters are permitted.
| Type: | String[] |
| Position: | 0 |
| Default value: | None |
| Accept pipeline input: | True (ByPropertyName, ByValue) |
| Accept wildcard characters: | True |
Inputs
You can pipe a string to the Get-FileHash cmdlet that contains a path to one or more files.
Outputs
Create Hash Key
Microsoft.Powershell.Utility.FileHash
Get-FileHash returns an object that represents the path to the specified file, the value of thecomputed hash, and the algorithm used to compute the hash.